Salesforce is the World’s number one CRM and is utilized by a diverse range of companies across various industries, encompassing a total of 150,000 enterprises. This powerful tool enables businesses to consolidate all their functions into a unified system. Notably, 62% of Salesforce clients are based in the USA, including prominent organizations such as Spotify, Amazon Web Services, and U.S. Bank. (Source- Salesforce and Statista)
These companies primarily trust Salesforce due to the strong “Trust factor” that Salesforce offers. Salesforce makes sure that the data their customers are entrusting them with is not going anywhere, and is safe as a vault. In this blog, we are going to dive deep into the importance of data security and how Salesforce goes above and beyond to keep that data safe and secure in every manner possible, the Salesforce data security model as we call it.
The Importance of Data Security in Salesforce
Key Components of the Salesforce Data Security Model
1. User Authentication and Authorization
User Authentication
The very first layer is the user authentication and authorization layer, as the name itself suggests, it is to authenticate the identity of a user trying to access Salesforce.
Salesforce supports various authentication methods:
- Username and Password: The basic authentication asks for a unique username and password.
- Multi-factor authentication (MFA): Multi-factor authentication helps add an additional layer of security by requiring users to verify their identity using a second factor, such as a mobile device or security token.
- Single Sign-On (SSO): Single sign-on allows users to authenticate only once and gain access to multiple applications without re-entering credentials, saving time on toggling between multiple windows over and over again.
User Authorization
Authorization determines what authenticated users are allowed to do within Salesforce. This is managed through profiles, roles, and permission sets:
- Profiles: Profiles specify the permissions that dictate a user’s access and interaction with Salesforce data.
- Roles: Roles establish the data visibility for users within the organization, structured hierarchically.
- Permission Sets: Permission sets grant additional permissions beyond the user’s profile settings, allowing for more detailed control.
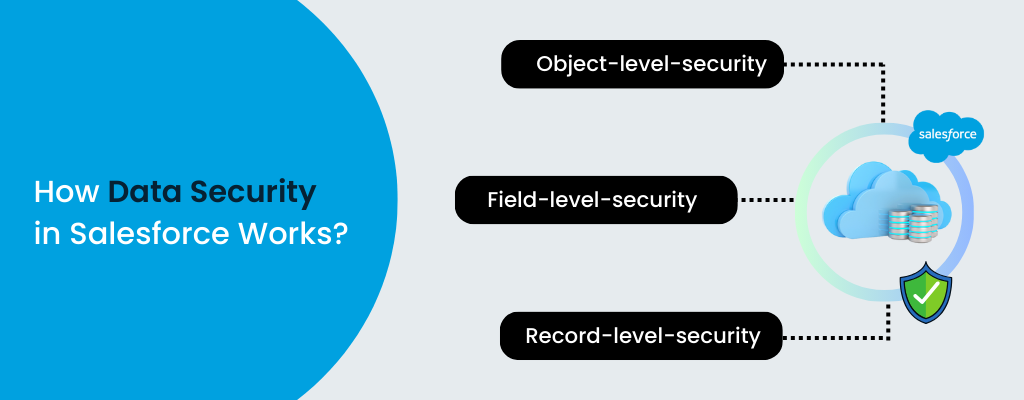
2. Object-Level, Field-Level, and Record-Level Security
Object-Level Security
Object-level security helps to control access to Objects in their entirety, such as Accounts, Opportunities, etc. The permission set takes care of which objects can be accessed by users.Field-Level Security
Field-level security restricts access to specific fields within an object. This level of security makes sure that users only see the information in sync with their role, nothing more, nothing less.Record-Level Security
Record-level security determines which individual records users can view and edit. This is managed through:- Role Hierarchies:Allow users to access records owned by users below them in the hierarchy.
- Sharing Rules: Define additional record access rules, enabling data sharing across roles, groups, or territories.
- Manual Sharing: Allows individual record owners to grant access to specific users.
3. Organization-Wide Defaults (OWDs)
Organization-wide defaults establish the foundational access levels for records in Salesforce. They dictate the standard visibility of records within an organization and can be configured to:
- Private: Only the record owner and users above them in the role hierarchy can access the records.
- Public Read Only: All users can view the records, but only the owner and users above them in the role hierarchy can edit them.
- Public Read/Write: All users can view and edit the records.
4. Salesforce Encryption and Shield
Salesforce Shield
Salesforce Shield provides an additional layer of security with three main components:- Event Monitoring: Tracks user activity and provides insights into potential security threats.
- Platform Encryption: Encrypts data at rest, ensuring that sensitive information remains secure even in the event of a data breach.
- Manual Sharing: Allows individual record owners to grant access to specific users.
Salesforce Encryption
Salesforce Encryption is used to make sure that even if the data is in transit or is at rest, the data remains protected and is secure. It helps enterprises to encrypt and protect the data fields that are sensitive, which enhances data security without compromising on functionality.5. Auditing and Monitoring
Salesforce Shield
Salesforce provides robust auditing and monitoring tools to ensure data integrity and security:- Login History: The login history functionality tracks all the login attempts and helps to identify any unauthorized access attempted.
- Field History Tracking: Salesforce tracks the field history as well to record changes to specified fields, providing a historical record of modifications made to relevant data fields.
- Setup Audit Trail: With Audit Trail, Salesforce logs changes to the Salesforce setup configuration, ensuring accountability for administrative actions.
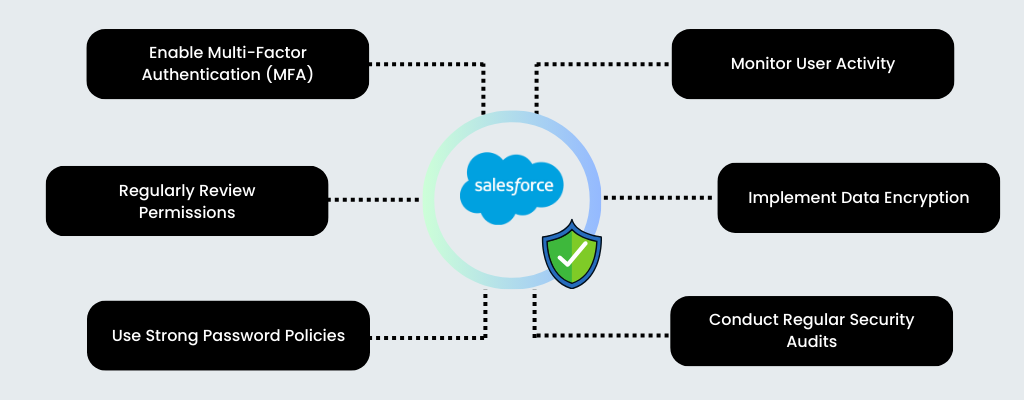
Best Practices for Ensuring Data Security in Salesforce
1. Enable Multi-Factor Authentication (MFA):
Try to enable the Multi-Factor Authentication to add an extra layer of security for user logins, making sure that the user identity is always maintained.
2. Regularly Review Permissions:
Always make sure that the user permissions are reviewed periodically to make sure that they align with current job roles and responsibilities.
3. Use Strong Password Policies:
Implement complex password requirements and take care that the passwords are regularly changed.
4. Monitor User Activity:
Utilize Event Monitoring to track user activity and identify potential security threats.
5. Implement Data Encryption:
Use Salesforce Shield Platform Encryption to protect sensitive data.
6. Conduct Regular Security Audits:
Periodically review and update security settings to address new vulnerabilities.
Wrap-Up
Understanding and implementing the Salesforce data security model is crucial for protecting any organization’s sensitive information. By leveraging Salesforce’s robust security features and following best practices, it can be ensured that the data remains secure and compliant with regulatory standards.
Talking about 200 OK, it is constructed on the robust Salesforce Einstein 1 platform, benefiting from all the security measures implemented by Salesforce. Consequently, choosing 200 OK ensures a high level of security. Furthermore, in the realm of AI, data security is crucial. CRM AI Copilot, built on 200 OK, also leverages these robust security features.
By leveraging the Salesforce data security model, you can maintain a strong security posture, protect valuable data, and build trust with your customers.